QilingLab – Release

Two years ago Ross Marks created the FridaLab challenge as a playground to test and learn how to use the Frida dynamic instrumentation toolkit.
At that time, I solved FridaLab and wrote a writeup about it explaining the main APIs and usages of Frida for Android. This helped others to start getting familiar with it and as a reference when developing Frida scripts.
After trying Qiling for some time I decided to follow Ross Marks’ steps and to develop a basic playground challenge to make use of the main Qiling features and I obviously called it QilingLab.
QilingLab is made of a GNU/Linux ELF binary compiled for either x86_64 and aarch64 (challenges are the same besides the 11th which is architecture dependent).
The binary is not stripped, not obfuscated, and compiled with gcc -O0.
⚠⚠ LAZY PEOPLE ALERT ⚠⚠
QilingLab has been developed with the aim of learning how to use Qiling by showing some use-cases.
That said all the challenges could be easily solved by just overwriting the checker but you know that’s cheating 👼🏾
The intended way of solving them is to enter / call the code which is responsible for setting the value which will pass the check!
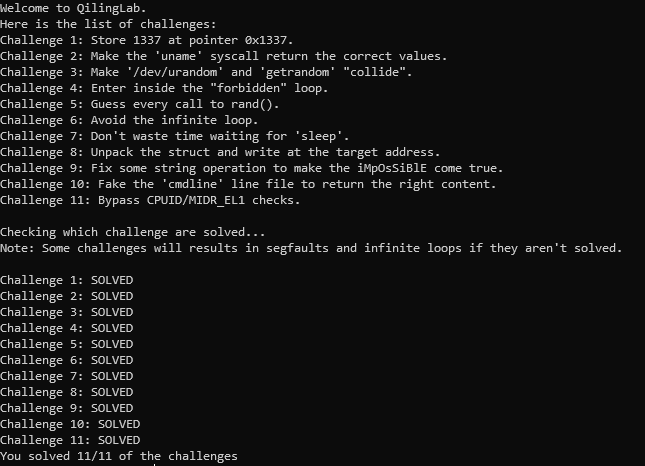
Challenges
Challenge 1: Store 1337 at pointer 0x1337.
Challenge 2: Make the uname syscall return the correct values.
Challenge 3: Make /dev/urandom and getrandom “collide”.
Challenge 4: Enter inside the “forbidden” loop.
Challenge 5: Guess every call to rand().
Challenge 6: Avoid the infinite loop.
Challenge 7: Don’t waste time waiting for sleep.
Challenge 8: Unpack the struct and write at the target address.
Challenge 9: Fix some string operation to make the iMpOsSiBlE come true.
Challenge 10: Fake the cmdline line file to return the right content.
Challenge 11: Bypass CPUID/MIDR_EL1 checks.
Ready, set, pwn!
Download the QilingLab challenge here:
x86_64 - aarch64
sha256sum qilinglab-*
a583c09cff06471fb38b93218d9cc7147279da1965491cdcf5b2d6e2c7b096d7 qilinglab-aarch64
711fd4517b8ae5d96bf8b3da144f74940b4f4f39b2d80e8884fbbf080bad8d89 qilinglab-x86_64
If you solve the challenges drop your writeup on Twitter and tag @ShielderSec and @qiling_io, we’d ❤ to see how you did it!